When it comes to threat detection in virtualised environments, security teams have several options based on three main monitoring approaches: agent-based, agentless, and hypervisor-based.
While the names point to how each method collects data – from inside, outside, or from the hypervisor layer – the differences go deeper and the type of monitoring used can influence everything from detection coverage and fidelity to operational overhead and scalability. For security teams tasked with protecting virtualised environments, understanding these models is essential to making informed decisions.
This article breaks down how each model works, explores their respective strengths and limitations, and helps security practitioners evaluate the right fit for their infrastructure and threat model.
What is agent-based monitoring?
Agent-based monitoring involves installing software components, or “agents”, directly inside each virtual workload. These agents run at the guest operating system level with system- or kernel-level privileges. They continuously monitor and collect data and events – such as process activity, memory usage, system calls, and file system changes – and send them to a central platform for threat detection and alerting.
Agent-based monitoring is commonly used in virtualised environments where in-depth visibility and runtime security are critical, or scenarios where organisations can manage the deployment and maintenance of agents.
Pros and cons of agent-based monitoring
Advantages of agent-based monitoring
- Real-time monitoring and reporting: Operating at runtime, agents provide continuous, real-time data collection and monitoring, enabling faster detection of incidents.
- Granular and detailed data: Agents can collect highly detailed information about system and workload states, offering deep visibility for the detection of process-level anomalies, in-memory attacks, and low-level system changes.
- Autonomous operations: Agents can function independently of central services, maintaining some level of monitoring even during network or platform outages.
Disadvantages of agent-based monitoring
- Risk of evasion or tampering: Because agents run inside the guest operating system, they operate within the same trust boundary. A sufficiently skilled or privileged attacker may evade, disable, or tamper with the agent to compromise its capabilities and evade detection.
- Coverage gaps: Security coverage is only as good as agent deployment; any missed or disabled agents, version drift or configuration errors, can introduce blind spots.
- Performance impact: Agents consume CPU, memory, and disk, which may affect the performance of the monitored system, especially in high-density virtual environments or resource-constrained systems.
- Operational overhead: Installing, updating, and managing agents across potentially hundreds or thousands of virtual machines and workloads can be time-consuming, error-prone, and adds complexity to security operations.
- Scalability challenges: Scaling agent-based solutions across dynamic or ephemeral environments can be complex and difficult to manage.
What is agentless monitoring?
Agentless monitoring refers to methods of collecting telemetry without deploying software agents inside each virtual machine or workload. Instead, it relies on external data sources and collection methods – such as telemetry data, network traffic, and API integrations – to gather information about system activity and centralise that information for analysis.
Agentless monitoring provides a wide surface-level view and is typically used for baseline visibility and posture management, particularly in large, cloud-native, or highly dynamic environments where workloads are frequently created, destroyed, or modified. However, it lacks runtime context and real-time capabilities, making it ineffective against fast-moving and runtime threats.
Pros and cons of agentless monitoring
Advantages of agentless monitoring
- Easy to deploy and maintain: There is no need to install and maintain software agents on each system, leading to faster setup, lower maintenance, and reduced operational friction.
- Reduced risk of tampering: Since agentless monitoring doesn’t rely on in-guest software, attackers can’t directly disable or manipulate the monitoring system.
- Scalability and flexibility: Agentless monitoring automatically scales to large, dynamic environments, such as cloud or virtualised infrastructures with ephemeral workloads.
- Broad coverage and visibility: Centralised monitoring through APIs or infrastructure logs enables a unified, infrastructure-wide view across multiple systems.
- Rapid time-to-value: Agentless tools can begin monitoring as soon as access credentials or APIs are configured, enabling organisations to quickly gain visibility without operational disruption.
- Minimal performance impact: With no in-guest components, there is no additional CPU or memory consumption on the monitored system.
Disadvantages of agentless monitoring
- Limited context and granularity: Without direct access to the guest operating system, agentless solutions cannot access granular, detailed data which are often necessary for advanced security use cases.
- No visibility into runtime threats: Agentless methods lack access to in-memory execution, process execution, or other runtime events within the workload, making them ineffective against runtime threats like fileless malware, rootkits, or memory-injection attacks.
- Lack of real-time detection: Agentless solutions typically operate by scanning disk images or snapshots at intervals, providing only point-in-time visibility which limits real-time detection and can miss short-lived or stealthy threats.
- Reliant on external data sources: Their effectiveness depends on the availability, granularity, and integrity of the APIs, logs, or telemetry feeds used, which can be delayed, incomplete, or manipulated by advanced threats.
- Risk of evasion: Without deep, real-time visibility, agentless methods may miss sophisticated threats, increasing the risk of detection gaps.
What is hypervisor-based monitoring?
Hypervisor-based monitoring operates from the hypervisor, outside the guest operating system, to observe the behaviour of virtual machines and workloads. While technically agentless, it differs in both method and depth. Rather than relying on logs or cloud APIs, it uses Virtual Machine Introspection (VMI) to observe virtual machines and their workloads at runtime, from the hypervisor, which is the the thin, privileged software layer that manages virtual machines on a physical host. This approach requires no software inside the workload yet enables visibility into memory, system calls, and kernel-level events that are typically only visible with agents. Because it sits below the guest OS (in what’s called ring -1), it offers stealthy, tamper-resistant, and privileged visibility into virtualised workloads.
Hypervisor-based monitoring is best suited for virtualised environments – especially in data centres, private clouds, and high-security or regulated industries, where in-guest monitoring is impractical or undesirable and where stealthy threats or privileged attackers may target virtual machines – because it provides strong runtime visibility and operational efficiency while reducing the risk of in-guest evasion or tampering.
Pros and cons of hypervisor-based monitoring
Advantages of hypervisor-based monitoring
- Strong isolation: The monitoring system resides outside the virtual machine, at the hypervisor level, offering architectural isolation from in-guest threats.
- Evasion- and tamper-resistant: Since it doesn’t rely on in-guest agents, it cannot be bypassed, disabled, or manipulated by in-guest threats – even if an attacker gains full control of the VM – making it highly effective against advanced attacks.
- Stealth by Design: Monitoring occurs invisibly from the guest's perspective, preventing a threat from altering its behaviour to evade detection since it doesn’t know it’s being watched.
- Deep runtime visibility: Hypervisor-based solutions can observe system calls, memory changes, kernel activity, and other runtime events, offering deep, real-time insight into system states and behaviours.
- Operational efficiency and scalability: A single monitoring system at the hypervisor layer can observe many VMs simultaneously and automatically monitor new VMs, reducing the need for per-VM agents and simplifying management in large-scale environments.
Disadvantages of hypervisor-based monitoring
- Designed for monitoring virtualised workloads: While suitable for both on-prem and cloud infrastructure, hypervisor-based monitoring is designed to observe virtual machines and workloads managed by a hypervisor (Type 1: bare metal, or Type 2: hosted). This does not extend to actual physical endpoints such as laptops and mobile devices.
- Hypervisor compatibility requirements: Effectiveness depends on the ability of the vendor to integrate with specific hypervisors, which may restrict flexibility or compatibility with an organisation’s virtualisation infrastructure.
- Deployment prerequisites: Unless hypervisor-based monitoring is already embedded and easily enabled by the virtualisation provider, implementing these solutions may require direct control over the virtualisation infrastructure.
Side-by-side comparison: agent-based vs. agentless vs. hypervisor-based monitoring
To better understand from where each monitoring approach operates, the diagram below shows where each type of monitoring solution is deployed in a virtualised infrastructure:
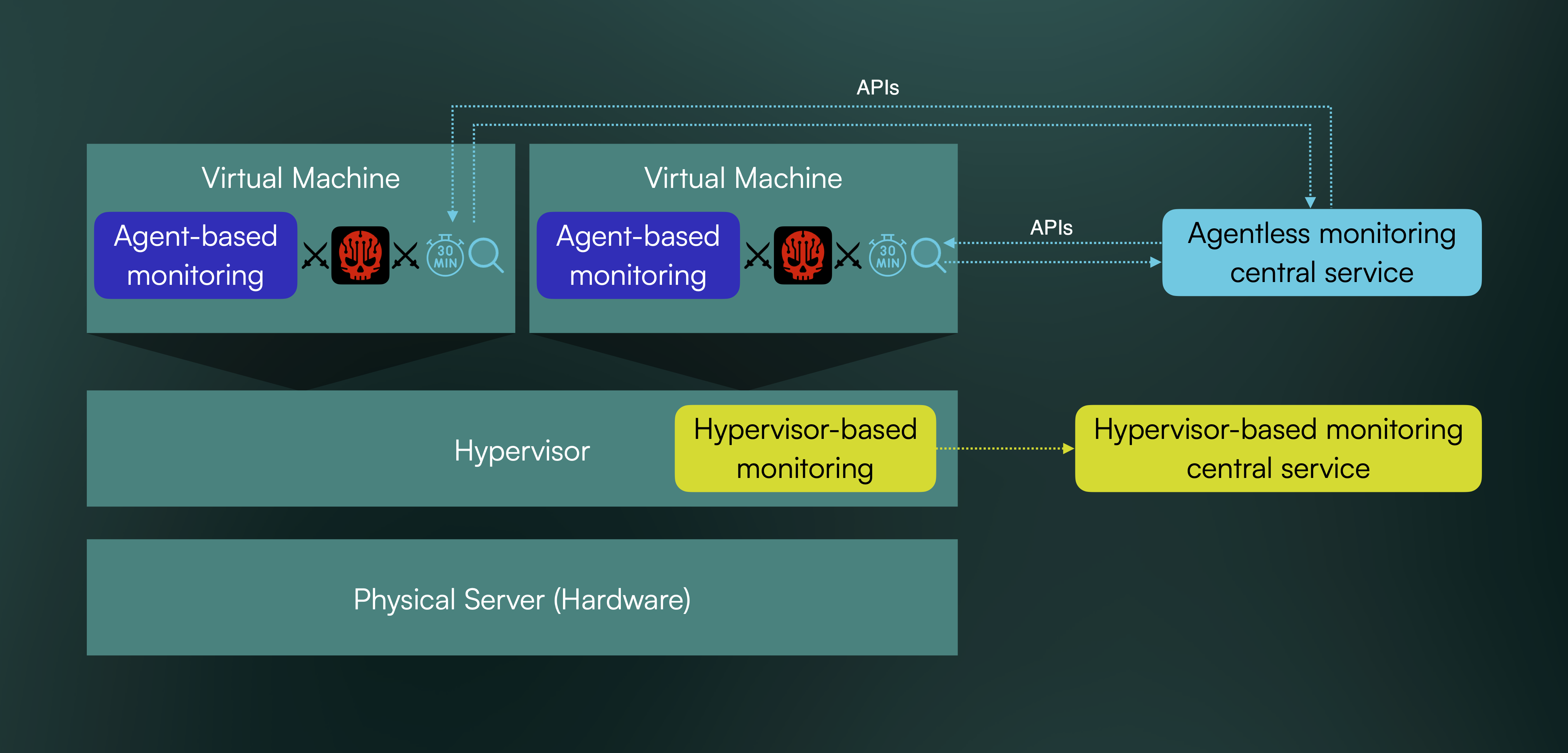
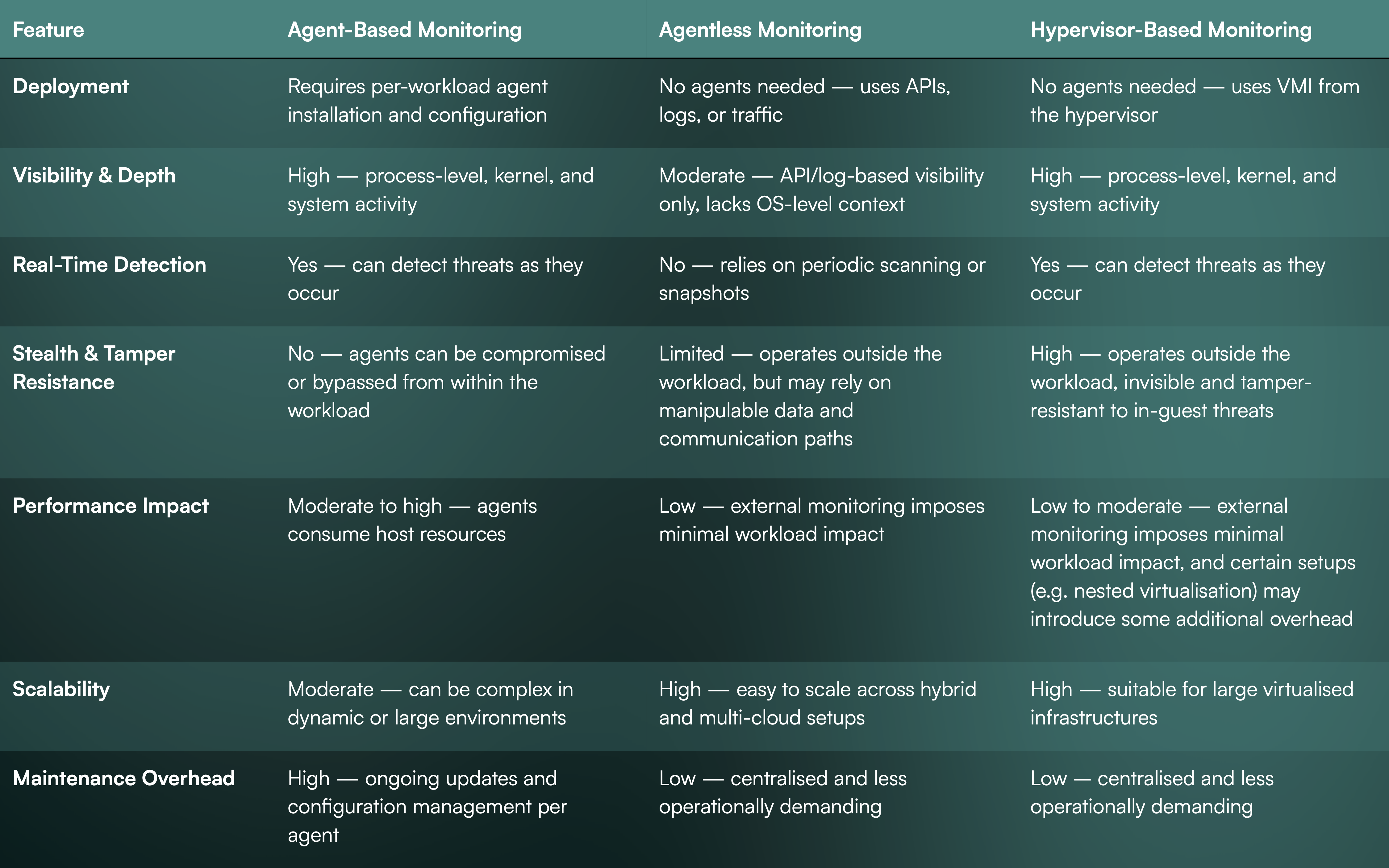
To help evaluate the differences across these three models, the table below compares their characteristics across key operational and security criteria:
Key considerations for choosing the right approach
When evaluating which model to adopt, security teams should assess the nature of their environment, operational constraints, security needs, and risk tolerance. Here are some important questions to consider:
- What workloads need coverage? Agent-based monitoring supports both physical endpoints and virtual machines. Hypervisor-based approaches apply exclusively to virtualised environments. Agentless methods work well across hybrid and multi-cloud setups. In complex or mixed environments, a layered monitoring approach may be necessary to achieve comprehensive coverage.
- What are your operational constraints? If your team cannot manage agents across the infrastructure, agentless or hypervisor-based monitoring may be easier to maintain at scale.
- How dynamic is your environment? Highly dynamic or fast-scaling environments often benefit from agentless or hypervisor-based monitoring.
- Do you need deep, real-time visibility? Agent-based and hypervisor-based solutions offer granular, real-time insight into runtime and in-memory activity.
- How critical is stealth and tamper resistance to your threat model? For high-security workloads or environments where attackers might gain elevated privileges, consider hypervisor-based monitoring to eliminate blind spots and ensure visibility persists even after compromise.
- Are you defending against sophisticated threats or compliance-driven risks? Hypervisor-based monitoring is particularly valuable in virtualised environments with stringent security requirements and strict compliance needs where advanced threats are a concern.
Conclusion
Agent-based, agentless, and hypervisor-based models each offer valid approaches, but their suitability varies based on what you're defending, the threats you're facing, and how your environment is structured.
In virtualised environments, hypervisor-based monitoring offers strong advantages: deep visibility, runtime awareness, tamper-resistance, and scalability from the infrastructure layer. For teams operating in high-security or compliance-driven settings, it may serve as an effective foundation for runtime threat detection and enable security teams to detect and investigate threats that other models may miss.
Ultimately, combining approaches where appropriate can help build a more resilient, scalable, and threat-aware security posture.
Considering hypervisor-based monitoring for your infrastructure? We help security teams evaluate how this approach fits into their environment. Contact us for a technical walkthrough or a tailored demo.




